In today’s hyperconnected retail environment, cyber incidents are no longer a matter of if, but when. Whether it’s ransomware halting supply chains, employee data leaked through a supplier breach, or reputational damage caused by insecure marketing systems, your ability to lead through the chaos defines whether your business emerges with resilience or regret.
As a CISO, I’ve lived this. And the most successful organisations don’t just respond—they learn, communicate, and evolve.
Who is this for
This article is for CEOs, CISOs, CIOs, risk executives, and board members in retail and consumer-facing businesses. If you’re accountable for customer trust, operational resilience, or shareholder confidence, this guide will help benchmark your readiness—and lead with clarity when it counts most.
CEO Snapshot: Why Incident Response Is a Business Imperative
- M&S lost hundreds of millions in market cap within days.
- 43% lower breach costs for companies with tested Incident Response (IR) plans (IBM 2024).
- Retail breaches now impact physical supply chains and stores.
- Brand damage often exceeds technical impact.
- Communication delays = social media outrage and regulatory scrutiny.
Bottom line: Poor IR isn’t just a tech issue; it’s an enterprise risk.
A well-structured Cybersecurity Incident Response (IR) program is not just a technical function—it’s a leadership imperative. As a CISO, I’ve seen firsthand how mature IR capability can protect customer trust, preserve business continuity, and drive strategic improvement. While elements of communication are often implied under sections like “Post-Incident Review” or “Human Factors,” it deserves its own dedicated spotlight, especially from a CISO perspective.
The most mature organisations align their Incident Response processes to globally recognised standards such as NIST 800-61, ISO/IEC 27035, and MITRE ATT&CK.
Let me take you through the six critical phases of incident response, illustrated with real-world events from across UK retail. Not to mention.
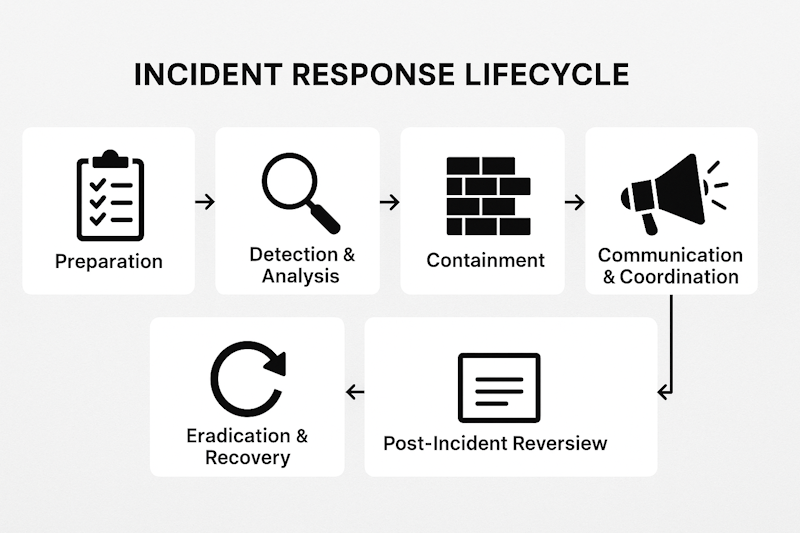
1. Preparation: Don’t Wait to Practice the Fire Drill
Incident response begins long before an incident. In retail, you’re balancing eCommerce platforms, POS systems, third-party logistics, and customer data—all potential entry points.
Remember Harrods in (2023)?
A third-party payroll vendor (Zellis) was breached via the MOVEit exploit, exposing Harrods staff data. Though the attack didn’t originate inside Harrods, their name was in the headlines. Those who had playbooks ready for supplier compromise were able to respond fast, notify staff clearly, and manage regulatory obligations.
Preparation means:
- Playbooks for direct and supplier-linked breaches
- Role-based escalation trees (HR, Legal, Comms)
- War room simulations for peak season scenarios
2. Detection & Analysis: Spotting the Unusual Before It’s Irreversible
What sets apart a strong Incident Response (IR) is early detection. From anomalous S3 bucket access to unauthorised privilege escalations, retail threat surfaces are broad.
Marks & Spencer (2025) confirmed it was hit by a cyber attack on its supply chain that affected food availability across several stores. Customers started noticing issues when they turned up to collect pre-paid orders, only to find missing items and empty shelves.
The culprit? A hacking group known as Scattered Spider—also referred to as UNC3944 or Muddled Libra. They’ve previously targeted major corporations using a mix of phishing, social engineering, and advanced ransomware techniques.
Best practices:
-
Monitor not just infrastructure, but user-facing systems
-
Leverage threat intel and ethical disclosures
-
Treat reputational alerts like technical alerts—they often come first
In a world where operational outages go viral faster than press releases, your IR playbook must include every stakeholder, from IT and logistics to social media teams and store managers.
3. Containment: When Every Second Counts
Once confirmed, your job is to limit the blast radius—quickly and quietly.
Shortly after the M&S incident, Co-op (2025) found itself in the cybersecurity spotlight. But this time, it wasn’t shelves running empty or customer data exposed—it was a textbook example of early detection done right.
After identifying a potential cyber threat on its network, Co-op proactively shut down segments of its IT infrastructure. While stores continued operating and customers remained unaffected, back-office systems and call centres were briefly impacted.
Importantly, Co-op maintained open communication, assuring customers that no action was required, and confirming it was working closely with the National Cyber Security Centre (NCSC).
This was a masterclass in prevention over reaction. No headlines, no lost trust—just swift, silent professionalism.
Whether the breach is internal or via a vendor, containment in retail means:
-
Isolating compromised APIs, supplier links, or third-party SaaS
-
Cutting off SSO or token-based access
-
Informing frontline teams, fast
4. Eradication & Recovery: More Than Turning It Back On
Eradication isn’t wiping malware—it’s restoring trust in your environment.
JD Sports (2023) was a lesson in layered impact. A breach affecting 10 million customer records required full-scale recovery: forensic validation, identity monitoring for affected customers, and rebuilding backend processes.
To recover the right:
-
Restore from clean backups only
-
Run post-restore scans and monitoring
-
Stage reactivation in order of business criticality (eCommerce first, then store ops)
5. Communication & Coordination: Silence is Risk
Arguably, the most overlooked superpower in Incident Response is clear, timely communication.
In every case—from Harrods to JD Sports—the narrative around the incident mattered as much as the technical response.
Here’s what the best communicators do:
-
Activate internal war rooms (Slack, Teams, Zoom bridge, and any other channels – depending on breach type)
-
Deliver 2–4 hour cadence updates to executives and stakeholders
-
Prepare legal, regulatory, and customer messaging before the headlines break
-
Keep the board briefed on risk, not code
Strong communication can protect brand equity even during chaos.
6. Post-Incident Review: Turn the Pain into Process
If your Incident Response (IR) process ends when systems are back online, you’ve missed the opportunity.
Marks & Spencer, after facing scrutiny for insecure email practices, turned their “near-incident” into an opportunity to audit all customer-facing systems, without waiting for an actual breach.
Real IR maturity means:
-
A formal After-Action Review (AAR) within 5–10 business days
-
Updated risk register + funding requests tied to actual gaps
-
Metrics delivered to the board: MTTR, comms SLAs, vendor accountability
CEO & Board Briefing Checklist
Ask yourself and your executive team:
- Have we tested our Incident Response(IR) plan within the last 6 months across all departments?
- Can we identify and isolate supplier risks in real-time?
- Does our Incident Response (IR) plan include store ops, customer service, and media comms?
- Are our legal, HR, and PR teams trained in breach scenarios?
- Have we turned past incidents into funded improvements?
If any answer is “no,” your Incident Response (IR) isn’t board-ready.
Final Thoughts: You Don’t Need to Be Perfect—Just Ready
Retail isn’t just about footfall and checkout conversion anymore. It’s about trust. And when that trust is challenged by a cyber incident, the organisation that can respond with confidence, clarity, and speed will lead the sector forward.
If you haven’t tested your response in the last 6 months.
If your suppliers don’t have breach communication protocols.
If your board only hears from cyber during audits.
You’re not ready. But you can be.
Make incident response a business function. Not a panic-driven reaction.
From chaos to control—it starts with leadership.
References
-
NIST SP 800-61 Rev. 2 – Incident Handling Guide
-
MITRE ATT&CK Framework – Threat behaviour mapping
-
Verizon DBIR 2024 – Retail breach trends

